Android / Apple / Artificial Intelligence / Business Intelligence / Cloud Security / Cybersecurity / Digital Media / Distro Reviews / Enterprise Software / Internet / Networking / New Downloads / News / Office Technology / Open source / Security / Self-Hosting Tools / Social Media / Software / Technology / Wearable Tech
Weak Hashing Algorithms (MD5, SHA1) – Easily Crackable Password Hashes
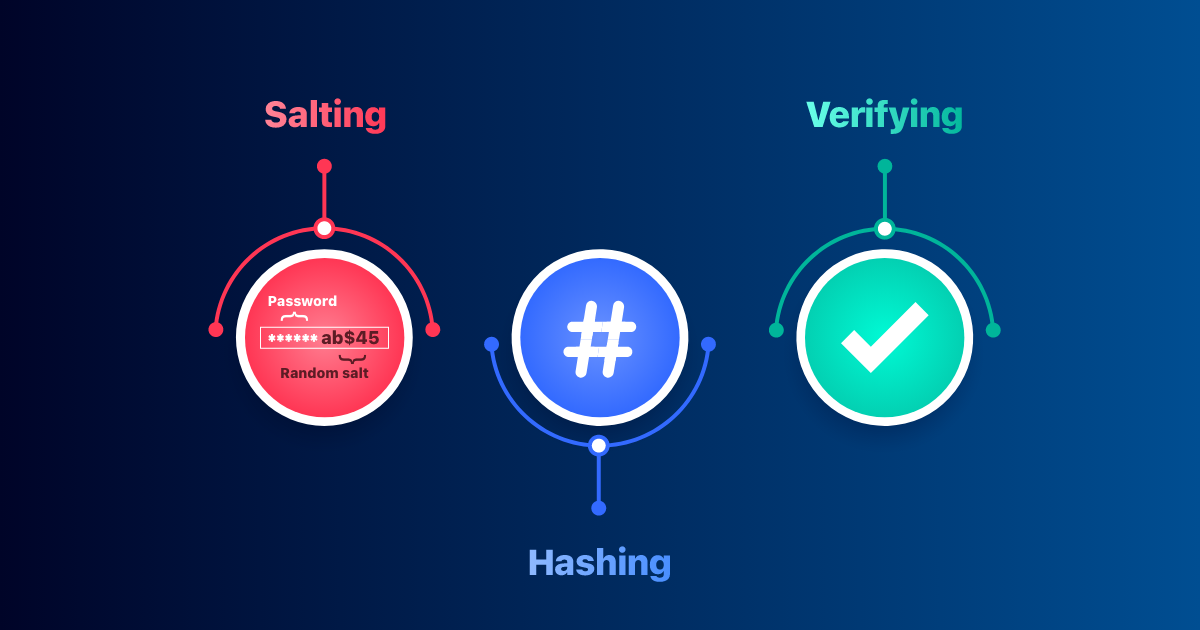
Introduction In the world of cybersecurity, password storage is a critical aspect of protecting user data. One of the oldest and most common methods of securing passwords is hashing—a process that converts plaintext passwords into irreversible strings of characters. However, not all hashing algorithms are created equal. Some, like MD5 (Message Digest Algorithm 5) and SHA1 (Secure Hash