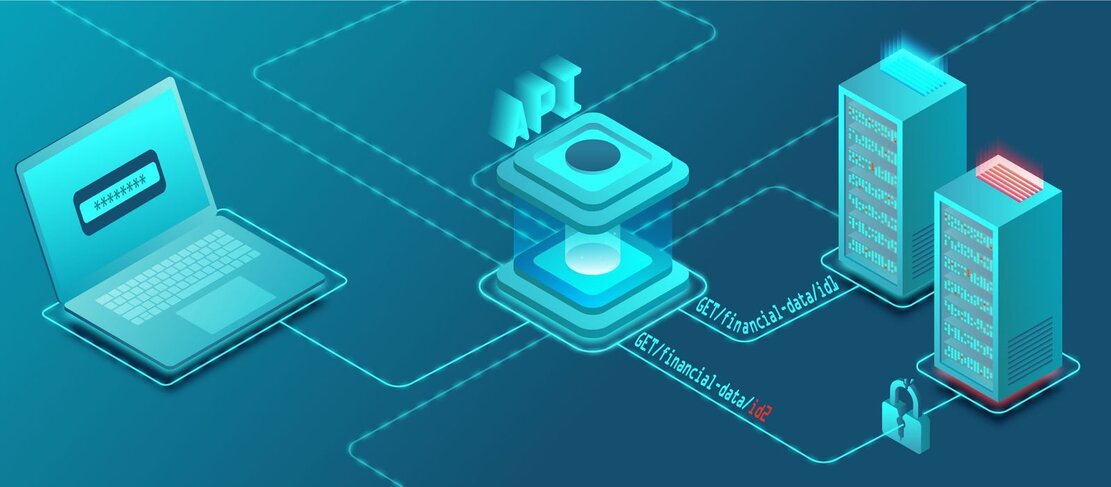
Broken Object Level Authorization (BOLA): How Attackers Exploit Object IDs to Access Unauthorized Data
Introduction In today’s digital landscape, APIs (Application Programming Interfaces) play a crucial role in enabling seamless communication between different software systems. However, with the increasing reliance on APIs, security vulnerabilities have also surged. One of the most critical and commonly exploited API vulnerabilities is Broken Object Level Authorization (BOLA). BOLA occurs when an attacker manipulates object